What is Telex?
Telex is a next generation Internet freedom technology. It's designed to help citizens of repressive governments freely access the online services and information of their choice. The Telex approach differs from other tools available today: Rather than working at network endpoints, Telex works through Internet service providers and other operators of core Internet infrastructure, which helps make it very difficult to detect and block.
Update (2018)
Telex has evolved into Refraction Networking, which is now deployed at ISP scale.
What makes Telex different from previous approaches:
- Telex operates in the network infrastructure — at any ISP between the censor's network and non-blocked portions of the Internet — rather than at network end points. This approach, which we call “end-to-middle” proxying, can make the system robust against countermeasures (such as blocking) by the censor.
- Telex focuses on avoiding detection by the censor. That is, it allows a user to circumvent a censor without alerting the censor to the act of circumvention. It complements services like Tor (which focus on hiding with whom the user is attempting to communicate instead of that that the user is attempting to have an anonymous conversation) rather than replacing them.
- Telex employs a form of deep-packet inspection — a technology sometimes used to censor communication — and repurposes it to circumvent censorship.
- Other systems require distributing secrets, such as encryption keys or IP addresses, to individual users. If the censor discovers these secrets, it can block the system. With Telex, there are no secrets that need to be communicated to users in advance, only the publicly available client software.
- Telex can provide a state-level response to state-level censorship. We envision that friendly countries would create incentives for ISPs to deploy Telex.
The Problem
Government Internet censors generally use firewalls in their network to block traffic bound for certain destinations, or containing particular content. For Telex, we assume that the censor government desires generally to allow Internet access (for economic or political reasons) while still preventing access to specifically blacklisted content and sites. That means Telex doesn't help in cases where a government pulls the plug on the Internet entirely. We further assume that the censor allows access to at least some secure HTTPS websites. This is a safe assumption, since blocking all HTTPS traffic would cut off practically every site that uses password logins.
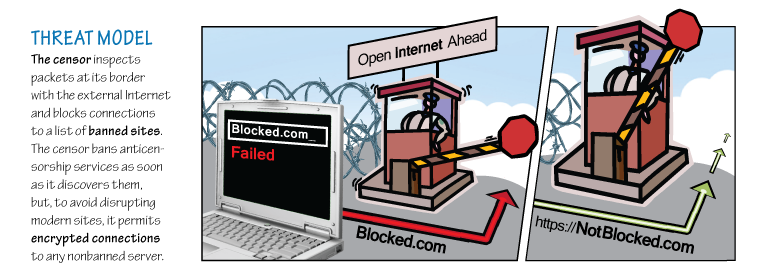
Many anticensorship systems work by making an encrypted connection (called a “tunnel”) from the user's computer to a trusted proxy server located outside the censor's network. This server relays requests to censored websites and returns the responses to the user over the encrypted tunnel. This approach leads to a cat-and-mouse game, where the censor attempts to discover and block the proxy servers. Users need to learn the address and login information for a proxy server somehow, and it's very difficult to broadcast this information to a large number of users without the censor also learning it.
How Telex Works
Telex turns this approach on its head to create what is essentially a proxy server without an IP address. In fact, users don't need to know any secrets to connect. The user installs a Telex client app (perhaps by downloading it from an intermittently available website or by making a copy from a friend). When the user wants to visit a blacklisted site, the client establishes an encrypted HTTPS connection to a non-blacklisted web server outside the censor’s network, which could be a normal site that the user regularly visits. Since the connection looks normal, the censor allows it, but this connection is only a decoy.
The client secretly marks the connection as a Telex request by inserting a cryptographic tag into the headers. We construct this tag using a mechanism called public-key steganography.This means anyone can tag a connection using only publicly available information, but only the Telex service (using a private key) can recognize that a connection has been tagged.
As the connection travels over the Internet en route to the non-blacklisted site, it passes through routers at various ISPs in the core of the network. We envision that some of these ISPs would deploy equipment we call Telex stations. These devices hold a private key that lets them recognize tagged connections from Telex clients and decrypt these HTTPS connections. The stations then divert the connections to anticensorship services, such as proxy servers or Tor entry points, which clients can use to access blocked sites. This creates an encrypted tunnel between the Telex user and Telex station at the ISP, redirecting connections to any site on the Internet.

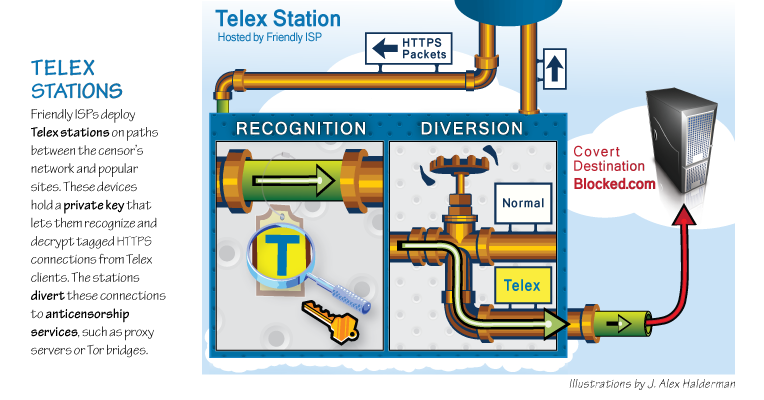
Telex doesn't require active participation from the censored websites, or from the noncensored sites that serve as the apparent connection destinations. However, it does rely on ISPs to deploy Telex stations on network paths between the censor's network and many popular Internet destinations. Widespread ISP deployment might require incentives from governments.
Development so Far
At this point, Telex is a concept rather than a production system. It's far from ready for real users, but we have developed proof-of-concept software for researchers to experiment with. So far, there's only one Telex station, on a mock ISP that we're operating in our lab. Nevertheless, we have been using Telex for our daily web browsing for the past four months, and we're pleased with the performance and stability. We've even tested it using a client in Beijing and streamed HD YouTube videos, in spite of YouTube being censored there.
Telex illustrates how it is possible to shift the balance of power in the censorship arms race, by thinking big about the problem. We hope our work will inspire discussion and further research about the future of anticensorship technology.
For more information, see our questions and answers section, read our technical paper, or contact us.

